Author: Ash Khan
-

How to Find and Fix Broken Authentication Vulnerability
Broken authentication is a vulnerability in security that happens when a program fails to properly authorize its users. This can result in illegal use of sensitive information, hacking of data, and other security risks. Broken authentication is a critical problem that has a substantial influence on website Security and can be fixed easily using Vulnerability…
-

How to Implement Real-time Data Sync with API Integration
Let’s dive a little deeper. Realtime does not always imply that anything is updated instantaneously (there is no one meaning of “instantly”). So, instead of focusing on the impact, let’s consider the method. Realtime is the automatic, synchronous, and simultaneous interaction between endpoints at a speed during API Integration. The concept of pushing data We’ll…
-
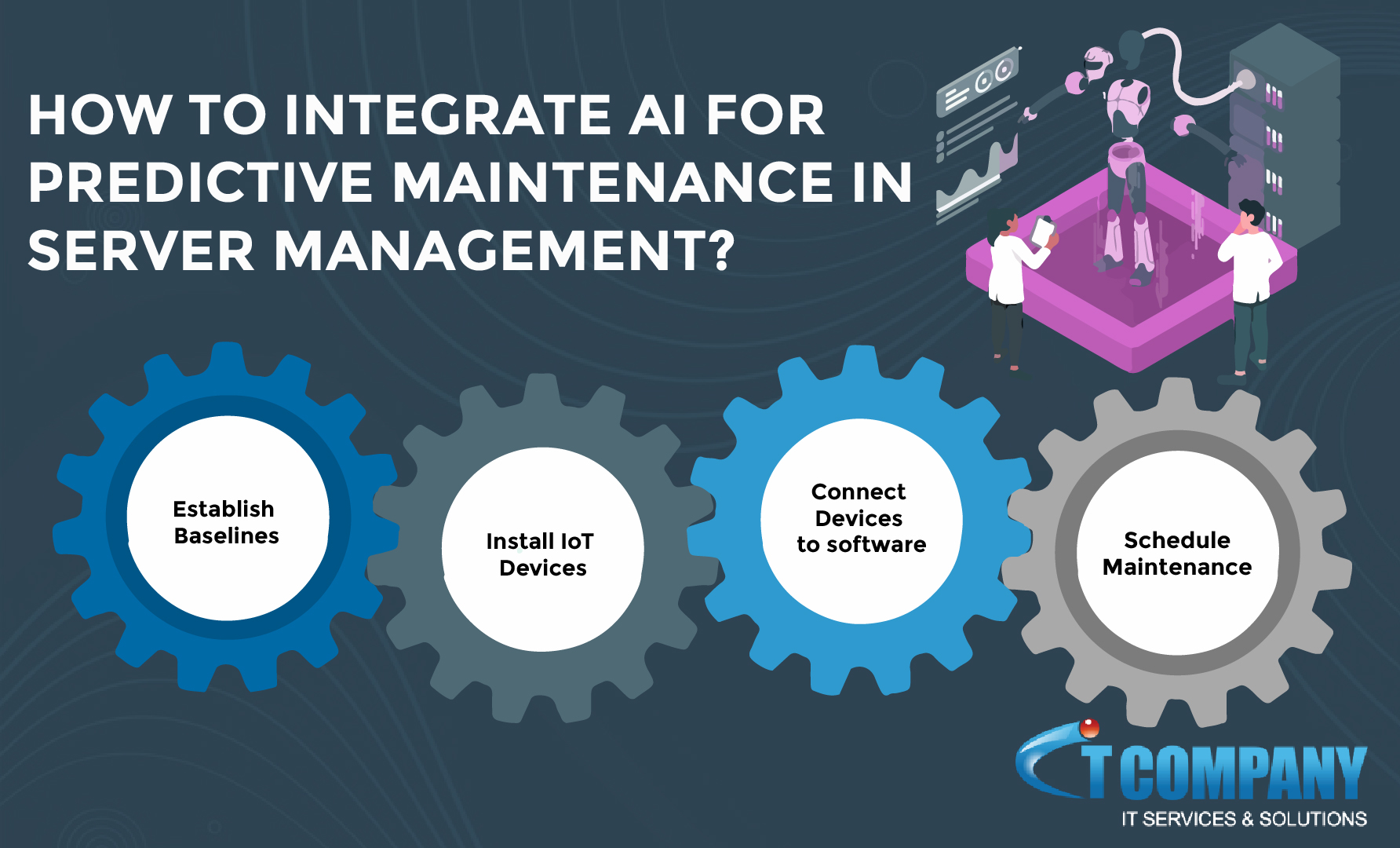
How to Integrate AI for Predictive Maintenance in Server Management
Server management is a critical aspect of any organization’s IT infrastructure. In today’s fast-paced digital world, the ability to predict server issues is crucial for maintaining uptime and reducing operational expenses. This is where the integration of artificial intelligence (AI) and predictive analytics can play a significant role. In this article, we will explore how…
-

WordPress Sites Infected with Balada Injector Malware Campaign
Since 2017, it’s been reported that over a million WordPress websites have been infected by malware known as Balada Injector. According to the cybersecurity website, various vulnerabilities in themes and plugins are abused in this comprehensive effort to compromise WordPress websites. Every few weeks, the attacks are known to occur in waves. Ongoing campaign The website security…
-

How to Deploy AI Machine Learning Models on Cloud VPS Server
Process automation is the first and most significant part of Cloud VPS Server that artificial intelligence may assist in enhancing. To be successful, a hosting company must integrate various elements into a single, well-functioning system. AI can automate everything from software development and integration to server management and customer service. Using AI to identify server faults…
-
Ultimate Guide to Choosing Your Premium DNS Provider
Welcome to our blog on selecting the most suitable DNS service provider for your organisation in 2024! In the modern age, when every click and keystroke counts, a dependable and efficient DNS service is critical to ensure smooth connectivity and peak performance. With so many alternatives available, choosing the best DNS service provider might seem difficult.…
-

How to Quickly Resolve Outlook Calendar Sync Issues in Microsoft Office 365
Do you have Outlook calendar sync troubles in your Microsoft Office 365 Business Premium? You’re not alone. Calendar synchronisation issues may be inconvenient, resulting in missed appointments, schedule conflicts, and reduced productivity. But don’t worry; in this tutorial, we’ll look at the most frequent reasons of Outlook calendar sync errors and present you with practical…
-

Troubleshooting 404 Errors in Web Maintenance
Welcome to our article on dealing with 404 problems during web maintenance in 2024! Consider this scenario: your website is undergoing standard maintenance, and your visitors receive the dreaded 404 page not found message. In this blog, we’ll look at the most common causes of 404 errors during Web maintenance and offer practical solutions that ensure…
-

How to Check & Optimize Email Security for Small Businesses with Limited Resources
For small businesses with limited resources, managing the complex field of email security may appear to be a difficult task. In this article, we’ll look at how small businesses may improve their email security, even with limited resources, by leveraging the capabilities of Email Security Check to protect their digital assets. Email threats are increasing…
-

Test for Server-Side Vulnerabilities with Website Security Tester
In modern internet-based globe, protecting your online assets from cyber attacks is critical. Server-Side Request Forgery (SSRF) vulnerabilities remain a major danger to online applications. As organisations work to strengthen their defences, staying ahead of these sophisticated threats necessitates professional expertise and cutting-edge technology. That’s where our Website Security Tester comes in. In this article,…
